Seamless compliance: strengthening IT security and managing risks in a targeted manner
In today’s business world, compliance is indispensable for companies - it has long been far more than just an item on a checklist. But how can companies meet the constantly growing regulatory requirements without losing flexibility and efficiency? One possible answer lies in an intelligent, digital tool such as a platform for Digital Employee Experience Management (DEX).
Why compliance is crucial
Compliance means ensuring that a company adheres to all legal and regulatory requirements. These include information security, data protection, availability, data retention and industry-specific standards. Failure to comply with these requirements can not only have legal consequences, but can also result in significant financial losses. However, compliance not only serves to avoid sanctions, it is also a decisive factor in building and maintaining a trustworthy corporate reputation. In practice, however, implementation is often difficult: confusing processes, a lack of transparency and a lack of real-time insights present companies with major challenges.
Nexthink is the market leader in DEX software and offers companies in-depth insights into their digital infrastructure. The platform not only enables targeted optimization of IT performance, but also effectively supports the implementation of compliance and risk management strategies.
How the DEX Platform Can Support You
- Real-Time Monitoring for Greater Transparency: A common obstacle to meeting compliance requirements is a lack of transparency. Nexthink provides a comprehensive overview of your digital infrastructure, enabling you to identify and address potential risks—such as unauthorized software installations or security vulnerabilities—at an early stage.
- Automated Reporting: Manual reporting can be time-consuming and error-prone. Nexthink automates this process and generates accurate reports tailored to your specific compliance requirements. This ensures you are well-prepared for audits and inspections.
- Proactive Issue Resolution: Nexthink not only helps identify problems but also enables proactive resolution. For example, the platform can send notifications when security-relevant software updates are pending—an essential contribution to maintaining IT security standards.
- User-Centric Perspective: Compliance is not only about systems but also about the people who use them. Nexthink helps companies analyze user behavior and steer it to ensure policy adherence—whether through the automatic removal of unauthorized applications or targeted awareness campaigns.
- Scalability and Flexibility: Whether you’re a mid-sized business or a global enterprise, Nexthink can be flexibly scaled and tailored to your individual requirements. This ensures your company remains agile and compliant, even as regulatory demands evolve.
Concrete application examples
Nexthink provides a wide range of reports, dashboards and actions ready-made in a Library (external link). Below are some examples of use:
With the Device Compliance package, Nexthink offers tools for checking device compliance in terms of administrator rights, software versions and security policies. This package provides a comprehensive overview of the compliance status of devices, covering areas such as system, software and network compliance. Each aspect is scored so that a simple numerical value reflects the compliance status. Detailed insights are also possible, for example into the differentiation between local and remote employees, device types, locations, models and operating systems.
A crucial aspect of compliance is protection against so-called shadow IT, i.e. uncontrolled IT resources that are used outside of official company guidelines. The platform shows which applications and cloud services are being used unofficially in your IT environment, such as cloud storage, VPN services or AI tools. This reduces security risks and ensures that all systems comply with company guidelines.
Another critical area is ensuring compliance of System Center Configuration Manager (SCCM) clients on all endpoints. Nexthink makes it possible to identify devices without an SCCM client installed and reinstall the client if required. Regular checks can ensure the integrity of the SCCM implementation and close potential security gaps.
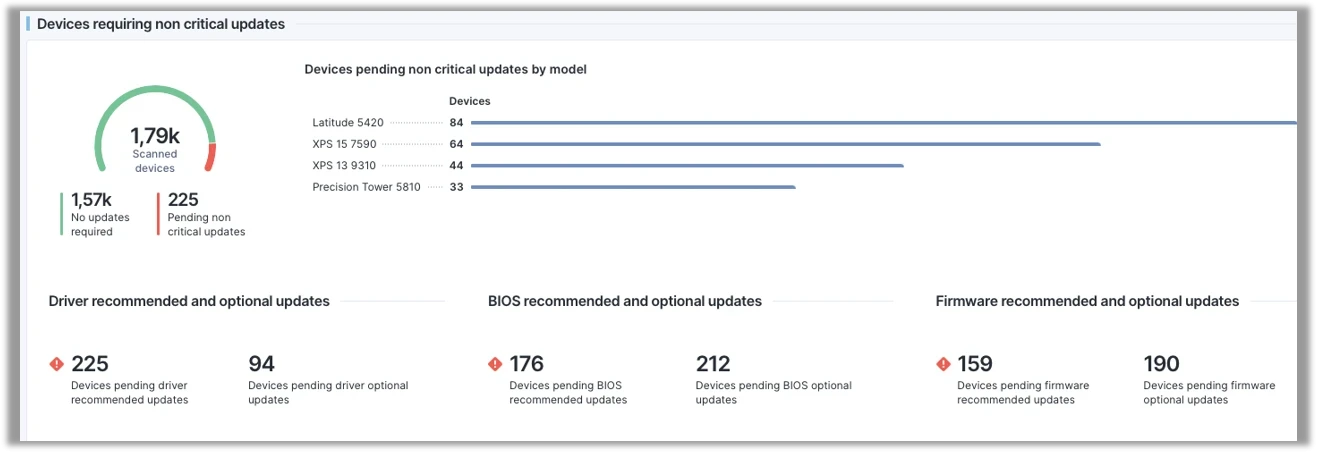
Example from practice: The following dashboard shows the status of devices that require non-critical updates. Out of a total of 1,790 scanned devices, 1,570 do not require any updates, while 225 devices require non-critical updates. The distribution of affected devices by model shows that the Latitude 5420 model is the most affected with 84 devices, followed by XPS 15 7590 (64), XPS 13 9310 (44) and Precision Tower 5810 (33). There is also a breakdown of what type of updates are still pending:
- Driver updates: 225 recommended, 94 optional
- BIOS updates: 176 recommended, 212 optional
- Firmware updates: 159 recommended, 190 optional
Compliance and security with Nexthink: IT optimization with expert support
Compliance should not be seen as a burden, but as an opportunity. Companies that see regulatory requirements as a strategic goal not only reduce risks, but also strengthen the trust of customers, partners and employees. With Nexthink, this is not only easier, but also much more efficient.
By providing real-time data, comprehensive analysis tools and proactive monitoring options, companies can optimize their IT infrastructure, minimize security risks and ensure that all regulatory requirements are met. In this way, Nexthink makes a decisive contribution to meeting compliance requirements and optimizing risk management, thereby making a significant contribution to a secure IT environment.
In order to exploit the full potential of Nexthink, it often makes sense to bring in external experts. As an experienced IT service provider, we support companies in the Implementation and optimization of the platform by adapting it to specific requirements, training IT staff and ensuring continuous monitoring of the IT environment. In this way, we ensure that IT meets compliance requirements and that risks are managed proactively.
Jens Reichardt
User Centic
E-Mail: jreichardt@spirit21.com
Jens is an expert in the field of device management and Modern Workplace. Whether it’s iOS, Android, Windows or macOS, you are in the best hands with Jens if you have any questions.




