Vulnerability management: security through vulnerability management
The four phases of vulnerability management
Vulnerability management consists of four phases. The first step is the detection of vulnerabilities. This can be done manually in very small environments by evaluating reports from a CERT such as the CERT-Bund. However, anyone who has ever tried this knows that the sheer number of reports and the manual check to see whether the exact version of an application affected is in use can quickly lead to an overload. This overload often means that the messages can no longer be processed or are simply ignored.
1. detection through the use of vulnerability management tools
The use of specialized tools is more convenient and effective. These are able to detect various aspects of a system. This can include the version and patch status of an operating system or an application, but also the configuration. A distinction is made between different scanning methods, depending on the system and the target to be achieved.
External Scans
External scans are a view of a system “from the outside”. Among other things, the following scans can be performed:
- Discovery of hosts: This determines all active hosts in the network. This is important to understand the scope of the systems to be scanned.
- Ports scanning: Scanning ports on the hosts can identify open ports and potential vulnerabilities. Open ports can indicate insecure services or outdated software.
- Website Scans: External web applications are scanned to identify vulnerabilities such as cross-site scripting (XSS), SQL injection and other attack vectors.
Internal scans
Internal scans occur within the network and use credentials to access systems. They include:
- Credential Scans: This uses credentials to access systems. This enables the identification of vulnerabilities that are only visible after successful authentication.
- Compliance scans: These scans compare systems against a baseline standard. They check whether the configuration complies with the security guidelines, for example whether the password policy is configured or the monitoring software is active. The technical components of norms and standards such as ISO/IEC 27001, the BSI IT-Grundschutz compendium or CIS benchmarks can also be checked.
2. assessment of vulnerabilities
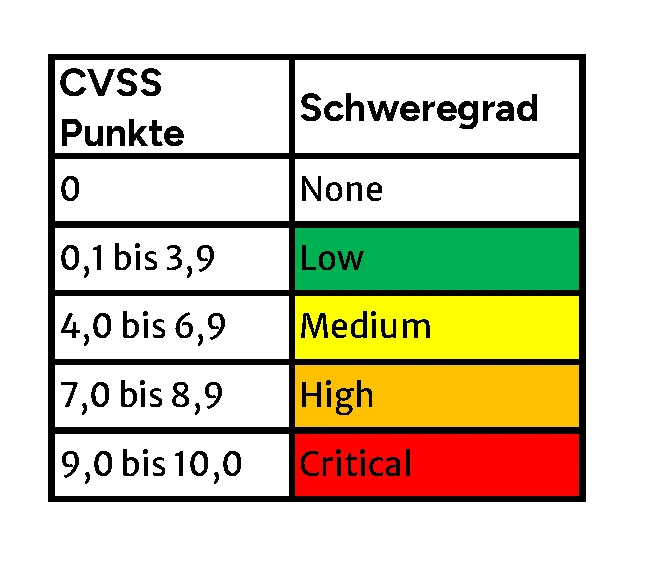
By using a tool to scan vulnerabilities, a general assessment is already carried out. This is based on the Common Vulnerability Scoring System (CVSS) and consists of several factors such as the attack vector, the complexity of a possible attack, whether interaction by a user is necessary and the affected protection goals. Depending on these factors, points are awarded, which can total between 0 and 10. The severity level is then derived from the points range.
The general assessment is therefore a good first point of reference for the assessment of vulnerabilities and can be used as the only indicator in many cases. However, some vulnerability management tools offer additional options for a more in-depth assessment. For example, it makes sense to first close vulnerabilities in systems that are publicly accessible, as in the example above. It is also possible to prioritize the treatment of vulnerabilities that have just been found to be actively exploited, e.g. by ransomware.
3. reporting
Vulnerabilities can be reported in a variety of ways. The vulnerability management tool usually visualizes the detected vulnerabilities on a web interface, but also makes them available via API or is able to independently generate tickets in the ticket system. The important thing here is to use the established method in the company wherever possible in order to achieve acceptance among the teams that have to rectify these vulnerabilities. The exclusive use of another tool can be counterproductive here. Instead, the web interface can provide more in-depth information, such as where exactly the vulnerability was identified, how it can be rectified or links to further information from the manufacturer.
4. Behebung: Herausforderungen beim Patchen
Die Behebung von Schwachstellen ist die letzte Aufgabe vom Lebenszyklus einer Schwachstelle. Zwar kann in seltenen Fällen die Akzeptanz möglich sein, jedoch wird üblicherweise ein Patch installiert oder ein Workaround implementiert.
Das Verteilen von Patches oder Implementieren eines Workarounds kann jedoch auch dazu führen, das ein System für die Zeit des Patchens nicht verfügbar ist oder das mit dem Patch ein Bug installiert wurde. Daher sollte auch hier abhängig von der Bewertung entschieden werden, ob dieser Patch schnellstmöglich verteilt wird oder aber erst zur nächsten geplanten Wartung des Systems. Zudem sollte abgewägt werden, ob zuerst ein Test in einer Testumgebung durchgeführt wird oder die Behebung direkt in der Produktivumgebung erfolgen soll.
Fazit
Das Schwachstellenmanagement ist von entscheidender Bedeutung, um Sicherheitsrisiken zu minimieren und potenzielle Bedrohungen abzuwehren. Durch die Identifizierung und Behebung von Schwachstellen können Organisationen ihre Sicherheit aufrechterhalten und ihre Ziele schützen.
Mehr erfahren

This blog post provides insights into the content of a live talk on the topics of Hybrid Work and Zero Trust.

In the virtualization of infrastructures, you sometimes reach the limits of what is possible. But workarounds are often possible.

How do you make a cloud environment both available at all times and secure against data loss?
Team SPIRIT/21
E-Mail: info@spirit21.com
The SPIRIT/21 team will be happy to advise you on all aspects of your IT tasks, from consulting and implementation to the operation of individual services and complete IT infrastructures. We deliver solutions that work. We look forward to hearing from you.

