App publishing: security & compliance always in view
In the third part of our series of articles on this topic Application Lifecycle Management, we want to take a closer look at the aspects of security, compliance and transparency. In the two previous articles, we looked at the various processes and challenges faced by the stakeholders involved and showed how processes can be accelerated and made more efficient through the use of special software.
As part of the app release processes, data and files have to be exchanged between the stakeholders involved in the organization time and again. E-mail, SharePoint, file shares and file transfer services are used for this purpose. Here you quickly come up against limitations in the size of attachments, blockages by virus scanners or missing authorizations. At the latest when external service providers, such as development or graphics teams, are involved, public sending via e-mail is ruled out and alternatives become necessary.
Incapptic Connect offers the option of mapping self-services and workflows with the stakeholders involved on a web interface, assigning granular rights and managing the app code and all associated metadata in a central location. There is no need to send data at all and all content remains securely within the company.
Centrally managed certificates increase security
Certificates are an indispensable part of the app release process. First and foremost is the so-called “distribution certificate”, which is provided by Apple or Google. It indicates to the outside world which company an app is assigned to. If this certificate falls into the wrong hands or Apple or Google suspect misuse, all applications ever signed with it lose their functionality. This represents a high risk and is all the more critical when you consider how these certificates are commonly used.
Companies usually start the mobilization of business processes through apps with small steps and a proof of concept. The aforementioned “distribution certificate” is therefore often created without further ado by an employee or external consultant and is then stored on the unsecured work device of one or more employees. Passing on this certificate to enable colleagues to quickly sign an app is quite common practice. Initially, this “start-up” mentality allows for quick results, but is in complete contrast to the established practices of e.g. SSL or S/MIME certificates in larger organizations. Here, only a very small group of people has access to the certificate material and the associated processes. Usually, however, this group of people has no points of contact with the app release processes.
This is where incapptic Connect comes in, as all the necessary certificates are encapsulated centrally in the system and are not available to the individual stakeholders. One less item on the CISO’s long list.
If you operate the app release process “by hand” with scripts and tools such as Fastlane, the lack of a role concept quickly becomes apparent. This applies not only to the processes within an organization, but also to the required interfaces and tools on the part of Apple and Google. The respective “Enterprise Developer Accounts” do not allow granular assignment of rights or integration into company directories. In addition, the number of possible accounts is not sufficient for larger organizations. It is not possible to differentiate between different departments or apps.
Incapptic Connect can encapsulate these functions and act as a central instance vis-à-vis Apple or Google. Access, roles and rights can be flexibly assigned for each department or external service provider. Access to the Enterprise Developer Account (Apple) can thus be managed centrally and does not have to be shared with different parties.
Security integrated from the outset instead of expensive retrofitting
The use of an integrated solution increases both transparency and traceability. Log files exist in a central location for all relevant processes. Audit trails make all changes traceable. Transparency is also created by the fact that the system provides an up-to-date overview of all rolled-out apps and their versions and provides installation figures for the product managers. In this context, UEM teams appreciate the automatic monitoring of the validity of certificates and provisioning profiles for a large number of apps.
In addition to secure processes, file storage and precisely defined access, another aspect is playing an increasingly important role: the security of the app itself. For example, it is important to check whether the app complies with internal guidelines for processing and storing data, adheres to coding guidelines or whether external developers have integrated unauthorized modules or even malware. In addition to employee and customer data, an organization could also be attacked from within.
The larger the target group of users, the more frequently apps are subjected to a risk analysis or pen test. This is carried out by highly specialized teams or external service providers and therefore represents another bottleneck in the app release process. In times of agile development and constant feature releases, bug fixes and security updates, in-house apps can practically no longer be subjected to continuous testing. Neither from a monetary point of view nor in terms of the availability of the necessary resources.
Automated risk analyses accelerate the app publishing process
The integration of automated risk and threat analyses can significantly facilitate compliance with guidelines and regulations and risks can be identified and assessed before rollout. Interfaces in incapptic Connect enable the integration of e.g. zScan from Zimperium directly into the build pipeline. This allows appropriate analyses to be carried out when the app is uploaded (e.g. by the developer) before the data even enters the further process flow. The code of the app itself is checked, the behavior of the app and which context the app uses, such as certificates, networks, domains.
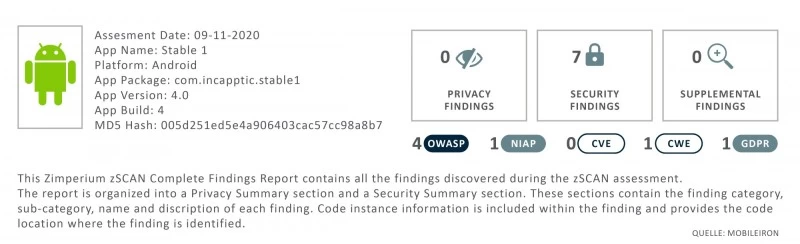
The following list shows some examples of possible approaches:
- Testing against best practices in the development and security environment such as OWASP, NIAP
- Securing communication and interfaces
- Use of SDKs that jeopardize privacy
- Outflow of sensitive data, use of cloud services
- Correct and secure compiler settings
- Access to API keys
- URL reputation
- Chain of trust, SSL validation, certificate pinning
You can read about the phases applications go through during their lifecycle and what is important in Part 4 of App Release to App Lifcycle Management.

Learn more

Application Lifecycle Management by SPIRIT/21 - Part 1: What processes are involved and which stakeholders are involved.

Application Lifecycle Management by SPIRIT/21 - Part 2: How processes can be designed efficiently and throughput times can be shortened.

App Lifecycle Management by SPIRIT/21 - Part 4: What is important for onboarding, deployment and deprovisioning.
Team SPIRIT/21
E-Mail: info@spirit21.com
The SPIRIT/21 team will be happy to advise you on all aspects of your IT tasks, from consulting and implementation to the operation of individual services and complete IT infrastructures. We deliver solutions that work. We look forward to hearing from you.

